Unmasking the Threat: Phishing & Spoofed Emails
With the evolution of technologies today, there have been many incidents of users falling for spoofing and phishing emails. According to phishing email statistics, approximately 3.4 billion spam emails are sent daily. In this blog post, we’ll provide the best practices to apply to your Microsoft 365 tenant to enhance your security to prevent users from receiving phishing and spoofing emails that could cause significant impacts within the company. Now, what is the difference between phishing and spoofing email?
Phishing Email
- Email phishing: The most common type of phishing attack. Cybercriminals impersonate companies or charities in an email, directing potential victims to click a link and enter personal information or pay for something. Any data entered can be seen by the cybercriminals, including passwords.
- Spear phishing: A targeted type of email phishing that uses personal information to craft more genuine-sounding messages.
- Whaling: A type of spear phishing in which cybercriminals target senior executives and high-ranking managers. These messages convey a sense of urgency, usually to transfer funds quickly.
- Smishing: Cybercriminals send text messages posing as a company or charity. These messages work much the same way as email phishing.
- Vishing: Cybercriminals call their targets and attempt to get them to give information, such as account credentials or credit card details, over the phone.
- Angler phishing: Cybercriminals use social media to get information, to get targets to visit a fake website or download malware.
Spoofing Email
Email spoofing is a technique used in spam and phishing attacks to trick users into thinking a message came from a person or entity they know or believe they can trust.
Social Engineering
Social engineering is a manipulation technique that exploits human error to gain private information, access, or valuables.
Implement DMARC, SPF, and DKIM
Implementing DMARC, SPF, and DKIM records on your Microsoft 365 tenant can help your organization’s email security. What does each of these protocols do for your tenant?
DMARC – Domain-based Message Authentication Reporting and Conformance (DMARC) is an email validation system that detects and prevents email spoofing. It helps combat techniques often used
in phishing and email spam, such as emails with forged sender addresses that appear to come from legitimate organizations.
DKIM – DomainKeys Identified Mail (DKIM) is an email authentication method that detects email spoofing. It enables the receiver to check that the owner of that domain authorized an email from a specific domain.
SPF – Sender Policy Framework (SPF) is an email validation protocol designed to detect and block email. It allows receiving mail exchangers to verify that incoming mail from a domain comes from an IP address authorized by that domain’s administrators.
Setting up DMARC, SPF, and DKIM on Your Domain
To enable DKIM for Microsoft 365, you have to meet the following pre-requisite.
– Publish two CNAME records on your domain registrar.
| Hostname: selector1._domainkey Points to address or value: selector1-<customDomainIdentifier>._domainkey.<initialDomain> TTL: 3600 |
| Hostname: selector2._domainkey Points to address or value: selector2-<customDomainIdentifier>._domainkey.<initialDomain> TTL: 3600 |
Enabling DKIM signing for your custom domain in the Microsoft 365 Defender portal
- In the Microsoft 365 Defender portal at https://security.microsoft.com, go to Email & Collaboration > Policies & Rules > Threat policies > Email Authentication Settings. In the Rules section > DKIM. To go directly to the DKIM page, use https://security.microsoft.com/dkimv2.
- On the DKIM page, select the domain by clicking on the name.
- In the details flyout that appears, change the Sign messages for this domain with DKIM signatures setting to Enabled ()
- Once completed, click Rotate DKIM keys.
Once you have DKIM enabled, you still need to train users to identify phishing and spoofing emails and potential social engineering. There are useful tools that can help you identify these potential risks when receiving emails, and one of them is using Message Header Analyzer.
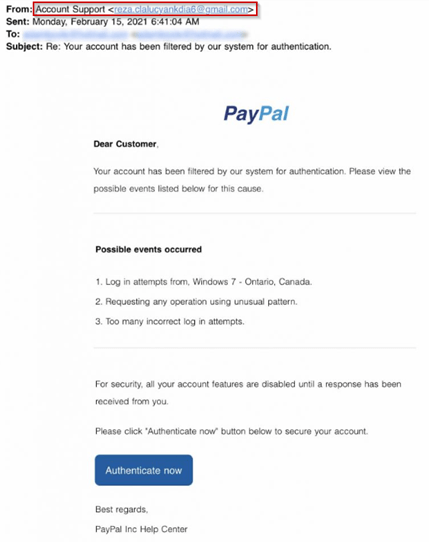
Scenario Example
In this example, you can see that the sender’s email address doesn’t align with the message content, which appears to be from PayPal.
However, the message looks realistic, and the attacker has customized the sender’s name field, so it appears in recipients’ inboxes as “Account Support”.
Other phishing emails will take a more sophisticated approach by including the organization’s name in the local part of the domain. In this instance, the address might read “paypalsupport@gmail.com”.
At first glance, you might see the word “PayPal” in the email address and assume it is legitimate. However, remember that the most important part of the address comes after the @ symbol, which dictates the organization that sent the email.
If the email is from “@gmail.com” or another public domain, you can be sure it has come from a personal account.
There’s another clue hidden in domain names that provides a strong indication of phishing scams – unfortunately, it complicates our previous clue.
The problem is that anyone can buy a domain name from a registrar. And although every domain name must be unique, there are plenty of ways to create addresses that are indistinguishable from the one that’s being spoofed.
Look at this example:
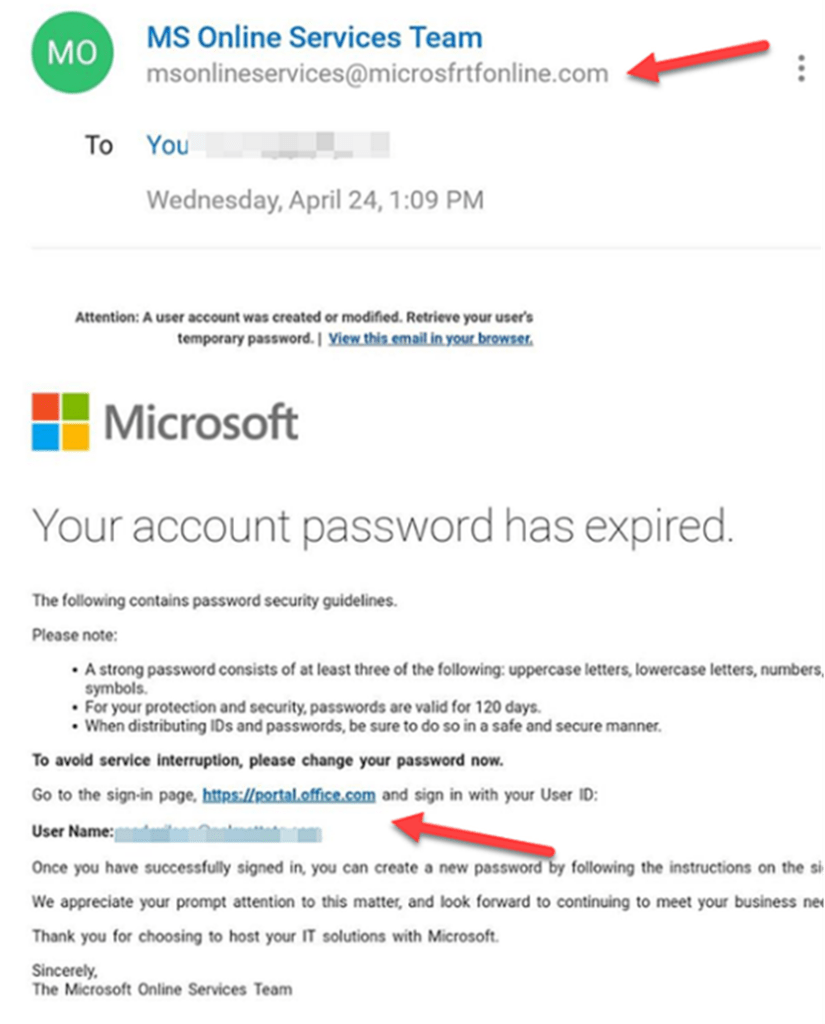
Here, scammers have registered the domain “microsfrtfonline.com”, which to a casual reader, mimics the words “Microsoft Online”, which could reasonably be considered a legitimate address.
Always be cautious with all emails you receive that you are not expecting or are unfamiliar with. If you’re unsure, please reach out to your IT department or a peer experienced enough to identify if it’s legitimate or not.
Thank you for reading this post! If you enjoyed it, I encourage you to check out some of our other content on this blog. We have a range of articles on various topics that I think you’ll find interesting. Don’t forget to subscribe to our newsletter to stay updated with all of the latest information on Imaginet’s recent successful projects
Related articles:
- Implementing External Email Tagging in Outlook
- Microsoft Office 365 Exchange Online Migration – Project Summary

discover more
QR Code Phishing Attacks: Are You Protected?
QR Code Phishing Attacks: Are You Protected? April 09, 2024 QR code phishing attacks or “Quishing” are on the rise, and it’s crucial to raise awareness about this evolving threat.…
Virtual Workspaces Are Here! How Will You Use Them?
Virtual Workspaces Are Here! How Will You Use Them? April 4, 2024 My YouTube feed has been full of reviews of the Apple Vision Pro since it became available in…
SharePoint Embedded: Full Featured SharePoint Inside a Custom Application
SharePoint Embedded: Full Featured SharePoint Inside a Custom Application March 28, 2024 Custom applications that require a lot of document management have always been a challenge to build. Historically, we…
Let’s build something amazing together
From concept to handoff, we’d love to learn more about what you are working on.
Send us a message below or call us at 1-800-989-6022.