Enhancing Remote Work Security with Global Secure Access (GSA) and Conditional Access Policies
July 25, 2024
What Is Global Secure Access?
Working remotely has become the norm for many people. Nowadays, people work from nearly anywhere, which makes network security even more important. Global Secure Access (GSA), available as a preview feature in the Microsoft Entra Admin Center, provides a solution for secure access to your apps and resources using Microsoft’s Security Service Edge (SSE).

Global Secure Access (GSA) can be used to control network traffic between endpoint devices and the internet. Capabilities of GSA include web content filtering, M365 traffic control, and can even act as a VPN for your private, corporate resources. The GSA client is installed on endpoint devices and helps forward network traffic to ensure secure data transmission. It uses Microsoft Entra ID to verify user identities, and users must authenticate before accessing resources, ensuring that only authorized users can connect.
GSA uses three traffic forwarding profiles. Microsoft 365 traffic forwarding profile handles SharePoint Online, Exchange Online, and Microsoft 365 Apps. The private access profile works with your corporate network, which can also act as a VPN for your private corporate resources. The internet access profile is for all other network traffic and can be used for web content filtering. In this article, we will go over requirements, and how GSA can be paired with Conditional Access Policies to block user access to M365 services on non-compliant endpoint devices, ensuring secure access.
Requirements, Activation, and Set up
Requirements for enabling GSA includes a Microsoft Entra ID P1 license, and at least a Microsoft 365 E3 license. To be able to configure GSA, you will need a Global Secure Access Administrator role. And to create Conditional Access Policies linked to GSA, you will need one of the following roles: Conditional Access Administrator, Security Administrator, or Global Administrator. Most importantly, endpoint devices need to be Microsoft Entra joined or Microsoft Entra hybrid joined to work with GSA. Microsoft Entra registered devices are not supported. The GSA client will need to be downloaded to necessary endpoint devices as well.
If this is your first-time implementing GSA, there will be a few things that need to be set up. On the Microsoft Entra Admin Center, find the Global Secure Access blade and go through the activation wizard. Under Connect > Traffic forwarding, you will see the three traffic forwarding profiles. We will only be working with the Microsoft 365 access profile in this article. Enable it by switching the button on beside its name. This setting will allow Microsoft Entra Internet Access to acquire the traffic going to all M365 services, except for Teams as it is not currently part of the common M365 endpoints and is not supported.
Downloading Global Secure Access on endpoint devices
Before downloading the GSA client, ensure that the endpoint device you are downloading it to is Microsoft Entra joined or Microsoft Entra hybrid joined. The GSA client will not work properly on Microsoft Entra registered devices.
In Microsoft Entra admin center, navigate to Global Secure Access (Preview) > Connect > Client download > click Download Client
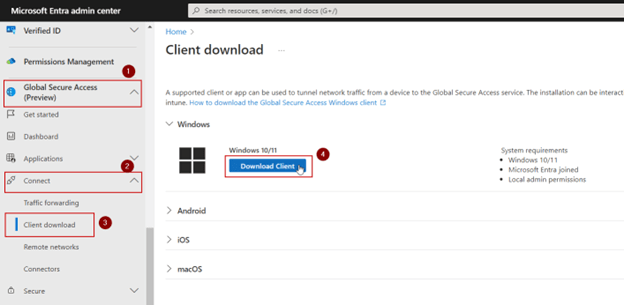
Alternatively, you can go to the link below to download the GSA Client for Windows 10/11.
https://aka.ms/GlobalSecureAccess-windows
Blocking traffic on an endpoint when Global Secure Access is off
If you want to control secure access to your resources, you can utilize GSA and Conditional Access Policies to block any traffic that isn’t going through the GSA client. This way, if a user tries to access M365 services on an endpoint that has the GSA client stopped or paused, the user will be denied access until they resume the GSA client. This will prevent M365 traffic from going through the public network and ensure that it only goes through the secured M365 channel using GSA.
In the Microsoft Entra admin center go to Global Secure Access (Preview) > Global Settings > Session Management > Adaptive Access > Enable Global Secure Access signaling in Conditional Access. This setting will enable you to create policies that restrict user access to specific apps based on their use of the GSA client.
To create the conditional access policy, expand the Protection blade > Conditional access > Create new policy. When configuring the Conditional Access Policy, use these settings:
Users: Specify users
Target resources: Select your preferred apps to block access to if GSA is not running. (e.g. M365 admin portals, Office 365, SharePoint Online, Outlook Online)
Condition:
Locations: Include Any location, Exclude Selected locations – All Compliant Network locations (GSA client network traffic)
Device platforms: Include Select device platforms – Windows
Access Control Grant: Block access
Enable Policy: ON
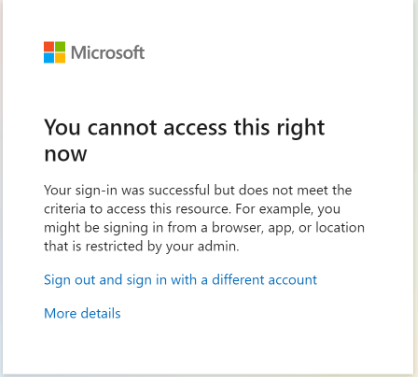
If one of the specified users tries to access a M365 resource listed in the Target resources without a running GSA client, they will be denied access and will be met with the message below. In order to gain access back, they will need to resume the GSA client.
Global Secure Access (GSA) offers a robust solution for secure remote access to apps and resources. By pairing GSA with Conditional Access Policies, organizations can enforce strict controls, ensuring that M365 services are accessed only through the secured channel provided by GSA. As remote work continues to evolve, prioritizing network security remains crucial, and GSA plays a pivotal role in achieving that goal.
Thanks for reading! We take cyber security very seriously. Make sure to subscribe to our blog to stay up to date on more technology safety tips, tricks, and updates.
Want to hear the latest from out team of experts? Sign up to receive the latest news right to your inbox. You may unsubscribe at anytime.

Discover More
Integration Between Power Platform and SharePoint Encourages Innovation
Organizations are focusing on innovation, streamlining their processes, and delivering better experiences for employees and customers. Power Platform and SharePoint are the Microsoft products that are helping organizations focus on…
Mastering Subagents in VS Code + Copilot: How To Actually Use Them
If you’ve ever dumped a giant problem into Copilot Chat and watched the conversation slowly turn into spaghetti, subagents are the feature you’ve been waiting for. Think of subagents as…
5 Common Misconceptions About Cloud Migration: Debunking the Myths
We’ve all heard of the cloud and cloud migration. But how important is it actually for your business? Organizations are moving to the cloud for several reasons: to improve agility,…

Let’s build something amazing together
From concept to handoff, we’d love to learn more about what you are working on.
Send us a message below or call us at 1-800-989-6022.





