Internet of Things: Are You Protected?
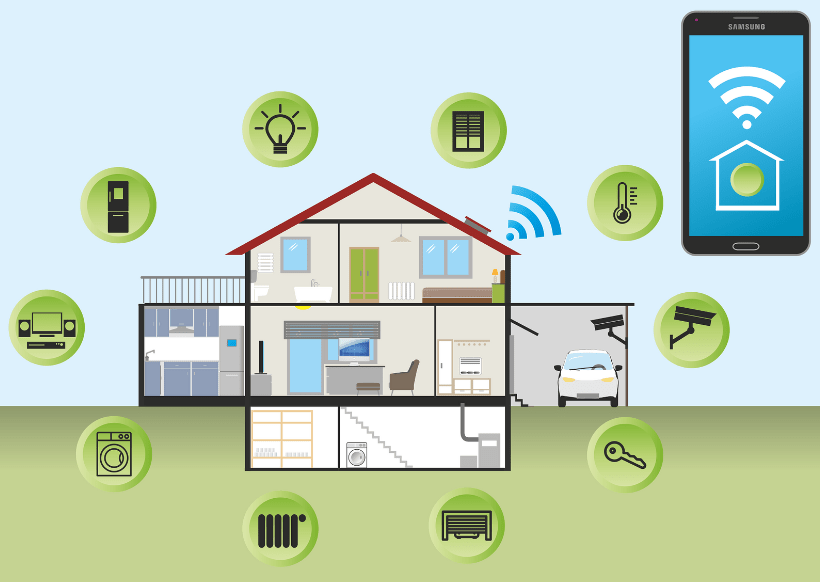
Internet of Things: Are You Protected? Simply put, the Internet of Things (IoT) are smart objects and can range from home devices (like Alexa) to complex industrial machinery and transportation systems. It is a network of physical devices or objects that are embedded with sensors, software, and network connectivity that allows them to collect and share data. How many people do you know who use some sort of smart device? My guess would be many. You yourself are likely to use some sort of smart device or technology. But have you stopped to think about the security risks associated with using these devices? How Does the Internet of Things Work? … Read more