Internet of Things: Are You Protected?
September 19, 2024
Internet of Things: Are You Protected?
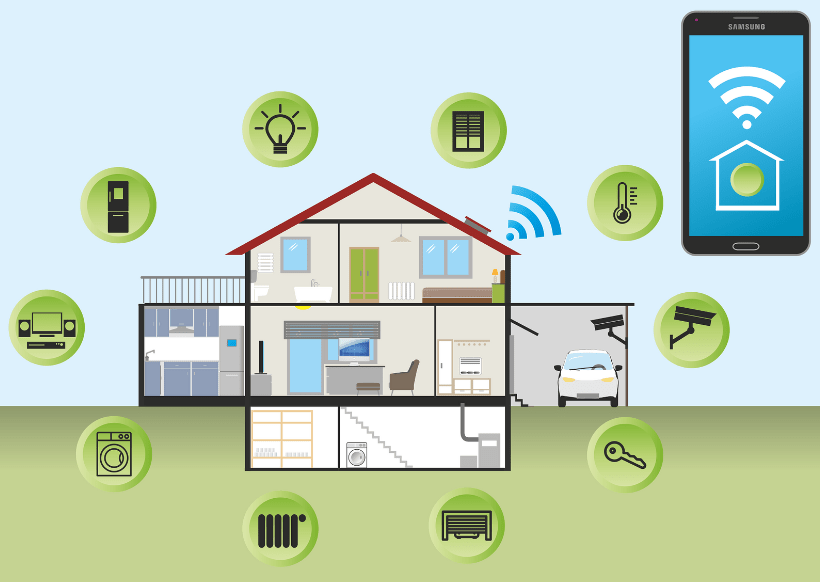
Simply put, the Internet of Things (IoT) are smart objects and can range from home devices (like Alexa) to complex industrial machinery and transportation systems. It is a network of physical devices or objects that are embedded with sensors, software, and network connectivity that allows them to collect and share data.
How many people do you know who use some sort of smart device? My guess would be many. You yourself are likely to use some sort of smart device or technology. But have you stopped to think about the security risks associated with using these devices?
How Does the Internet of Things Work?

IoT enables these smart devices to communicate with each other and other internet-enabled devices. This creates a massive network of interconnected devices that can exchange data with each other. IoT is used across many industries including manufacturing and healthcare.
For example, in healthcare, the IoT has helped improve efficiency, reduce costs, and enable data-driven decision making. Yet, IoT technology is growing rapidly and therefore how it impacts privacy and security needs to be taken into consideration. Furthermore, security should be considered by ALL smart device users. Not just those in the business world.
Key Risks Associated with the IoT
Below is a list of the security measures that need to be considered when using the IoT:
- Insecure Devices: Many IoT devices are shipped with default settings and insecure protocols, making them vulnerable to attacks. Attackers have exploited these weaknesses to gain unauthorized access to devices and the networks they are connected to.
- Data Privacy: IoT devices collect and transmit large amounts of data, including personal and sensitive information. If this data is not properly secured, it can be intercepted and misused by cyber attackers. Organizations must take steps to ensure data privacy is held to the highest standard. You must ask yourself if your customer/employee data is protected when using the IoT.
- Network Attacks: IoT devices can be used as entry points for network attacks. For example, compromised IoT devices can be used to launch Distributed Denial of Service (DDoS) attacks, which can disrupt the availability of services and cause significant damage.
- Obsolete Components: Some IoT devices use outdated software and hardware components that are no longer supported or updated. This makes them more susceptible to known exploitation by cyber criminals.
- Remote Work Risks: With the rise of remote work, securing IoT devices in home networks has become more challenging. Home networks often lack the level of protection found in corporate environments, making them easier targets for attackers.
These risks are relatively simple to mitigate. It is important to always adopt best practices like regularly updating your devices, changing default settings, using strong authentication methods, and implementing network segmentation to isolate IoT devices from critical systems. With just a few additional steps, you will be safeguarding your data and privacy from potential online threats.
Examples of IoT Security Breaches
If you think a cyberattack will never happen to you, think again. Cyberattacks happen because people get too comfortable, forget to implement proper safeguards, or lack the understanding of potential safety gaps.
Ring Home Security cameras experienced a security breach where hackers were able to access live feeds from cameras around customers’ homes. The hackers were even able to communicate remotely using the devices microphones and speakers (Jo Vanwell, Conosco). The thought of someone having access to you in the safety of your own home should be terrifying.
Similarly, smart baby monitors were being hacked, allowing people to spy on and even communicate with children (Jo Vanwell, Conosco).
These examples highlight the importance of securing IoT devices to prevent unauthorized access and potential harm.
Conclusion
Smart devices aren’t going anywhere. In fact, they are only going to get more advanced and therefore, should be used by people and organizations. The benefits are endless. However, it is important to keep the risks they pose in mind. Always ask yourself if you are doing enough to protect yourself, your organization, and your customers.
References: IoT Security Breaches: 4 Real-World Examples – Conosco
Have a project in mind? Our team can help. Fill out the form at the bottom of the page and someone will be in touch. Make sure to subscribe to our blog for more helpful technology tips, tricks, and updates.
Want to hear the latest from out team of experts? Sign up to receive the latest news right to your inbox. You may unsubscribe at anytime.

Discover More
Integration Between Power Platform and SharePoint Encourages Innovation
Organizations are focusing on innovation, streamlining their processes, and delivering better experiences for employees and customers. Power Platform and SharePoint are the Microsoft products that are helping organizations focus on…
Mastering Subagents in VS Code + Copilot: How To Actually Use Them
If you’ve ever dumped a giant problem into Copilot Chat and watched the conversation slowly turn into spaghetti, subagents are the feature you’ve been waiting for. Think of subagents as…
5 Common Misconceptions About Cloud Migration: Debunking the Myths
We’ve all heard of the cloud and cloud migration. But how important is it actually for your business? Organizations are moving to the cloud for several reasons: to improve agility,…

Let’s build something amazing together
From concept to handoff, we’d love to learn more about what you are working on.
Send us a message below or call us at 1-800-989-6022.